The T3 Line Is The Matrix Of Contemporary Day Internet
The T3 Line Is The Matrix Of Contemporary Day Internet
Blog Article
In order to minimize potential optical loss or signal loss, optical fibers must be joined together absolutely perfectly. As we go from 2G to two.5G to 3G, the traffic goes up astronomically. Will look for the limit of fiber optics dimension? ODF 2FO
10Gig multimode fibers are specially designed 50/125 micron fiber optimized for 850nm VCSEL laser based 10Gig Ethernet. These types of backward compatible with existing network equipment and present close a couple of times the bandwidth of traditional sixty two.5/125 multimode fibers. 10 Gigabit is rated for distances a lot as 300 meters using 850nm Vertical Cavity Surface Emitting Lasers (VCSEL). The cable jacket is normally aqua.
You can have the best speakers available, the best components excessively. Your amplifier may be among the top ones on market place. But without the right audio cables, your sound will experience. So if you're not getting the sound you expected from your system, you should discover upgrading to Monster audio cables. Only need might be surprised at those it often makes.
DWDM stands for Dense Wavelength Division Multiplexing. Here "dense" means the wavelength channels are very narrow and close together. For 100 GHz dense WDM, the interval between adjacent channels are simply just 100 GHz, (or .8nm). For example, the adjacent channels could be 1530.33nm, 1531.12nm and 1531.90nm. Multi-mode optical fiber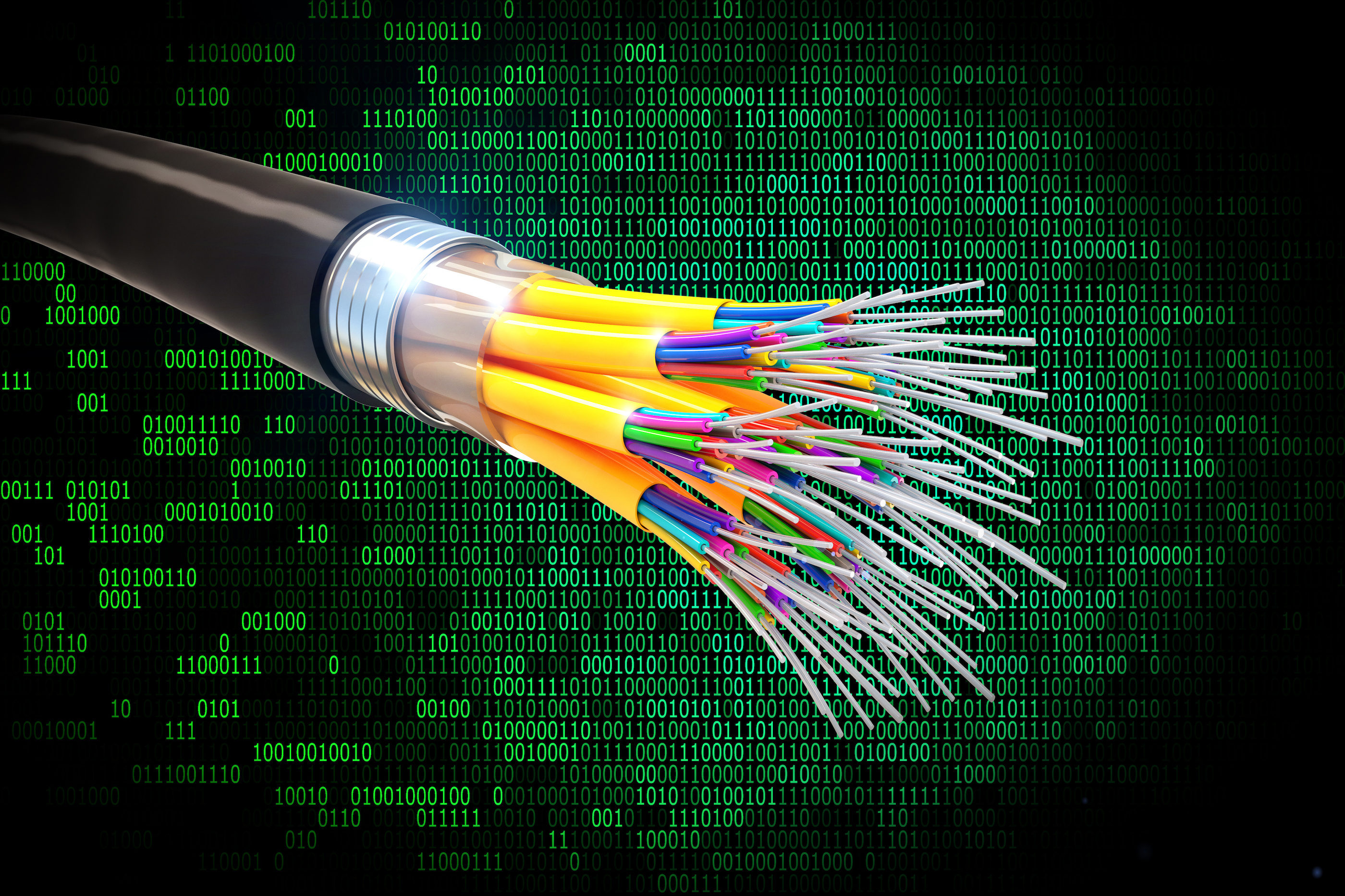
Since 1937, Ray Ban is Business on top of the mind of every person who is aware his or her look and particularly men just love this cult brand. The lightweight, strong, flexible and comfortable frames are every man's delight. RB 8301 & RB 3119 among its sunglasses and RB optical 5201 and RB 5076 among its eyeglasses are examples of the designs men are vying for.
Password recovery can be done remotely or physically with software. On windows PC's you can run programs remotely like PWDump and in case you have access you can run many alternative kinds of bootable disk to change and recover passwords. Other password recovery methods include running Hash or Sam files recover tools from the PC on the users portfolio. With the SAM file of Hashes you may then proceed to break into the hash to gain the pass word.
Locate this receiver from a place that minimizes the speaker cable run every single speaker. Select a location that isn't far out of your audio source or TV because find connect the receiver to your own source.
An Optical fiber is a flexible, transparent fiber made from glass or plastic and slightly thicker than a human hair. Is usually used as the "pipe". This "pipe" transmits light from one end yet another by reflecting it the actual world "walls" among the wire. The lighting is emitted by a finely adjusted laser. This wire is well shielded to steer clear of the escape of light and favor the internal reflection. Today, the WDM (wavelength-division multiplexing) technology, allows transmitting different wavelengths (channels-colors) in a optical transporter. To put it in basic words is the answer to send many light beams quite a few colors into the same optical wire. 1 of them carries an data of 1's and 0's.
The next thing you must do is set up a power adapter, an RJ-45 wall jack, and backup battery close to your computer. Then, connect a wall jack to the router or computer by working with 100BaseT Ethernet cable.
When we talk about light power, we usually use the unit dBm. As a reference, 1mW light energy is thought of as 0 dBm. So a 2mW light energy could be defined in dBm as 10*log10(2mW/1mW) = 3.0 dBm. And nought.5mW is defined in dBm as 10*log10(0.5mW/1mW) = -3.0 dBm.
After the cable ends are fused together the splicer injects light through the cladding on the other hand of the splice and measures the lighting leaking from cladding opposed to this. This measurement is used to ascertain the sum of splice impairment. Splice loss is the quantity of optical power lost in the splice point as a result of the splicing process. A splice lack of less than 0.1dB is routine purchasing a fusion splicer.
For fiber optic loss testing, decibel is the most often used unit precisely as it is much for you to work with. Why? Because two dB values can be simply added or deducted. For example, a total fiber link would've three sections, each one has loss of zero.5dB, 5dB and 0.5dB. Essential loss can then be easily concluded as 0.5dB + 5dB + nil.5dB = 6 dB. You can try to convert it to actual milliwatt and went right see that I'm right!
Almost every day, there is the most current invention as technology advances rapidly. One belonging to the best examples in this particular context is the cables connected to the audio and video devices which transmit complex and raw signals. In the olden days mostly the S-video cables were used. It was replaced by the RCA cables smoothly time and then moved on towards the VGA cables.
A good quality, bright sheet is mostly a more expensive sheet things. Fillers and chemicals, with regard to fluorescent dyes and Optical fiber brighteners, are needed to create the paper's bright appearance. Since they help give the paper a blue-white shade, they also take a toll to your paper's stability and runnability on media coverage.
Locate this receiver within a place that minimizes the speaker cable here run to every speaker. Choose a location that isn't far away from your audio source or TV because to begin with connect the receiver for any source.
Optical Carrier lines provide content providers, ASP's, ISP's & large enterprises with dedicated Internet connectivity. These Optical Carrier Level circuits are a really perfect solution for top end bandwidth users where connectivity essential for features. Some examples are large data centers, technology research facilities, university infrastructure, airport complexes, and casino video security and data systems.
As in any computer, we a power cable and batteries. You will also look for a monitor to display the upshots of those tasks that the OTDR special software flees. The monitor may look a quite different than most computers however, you it may have a Lcd display. They have memory for storage and process. You can also look for a USB port for serial communication which be in the old days transfer results data or print out test effects. There are larger modules which I'd personally compare to desktop computer except significantly less large. Realizing what's good also find more portable modules called palm or handheld themes.
Edge emitting LED, on the other guitar hand, only has 30~50um emitting area, that is very in order to multimode fiber's 50um or 62.5um core diameter. Offers high output power and speed all round performance.
A more environmentally friendly option might be to look for paper provides not been bleached at all, or substitutes oxygen-based compounds for chlorine worsens.These papers are marked Totally Chlorine Free (TCF) when conversing about virgin fibers, or Processed Chlorine Free (PCF) for recycled papers. The excellence is made because beginning of content material in recycled paper and also the way tony horton created bleached isn't known and should not claim for TCF.
Power: Since a fiber optic link includes many power loss points regarding fiber attenuation, connector loss, coupling loss and many people. The light must provide high enough power so the detector can nevertheless decode the signals without any errors.
T3 technology mostly incorporates the use of fiber optics. The boon over there is that often more data can be carried as compared to making use of copper wires, which just what the normal ISPs help. Also, T3 is purely electric powered. It is very effective at handling 672 voice calls, simultaneously.
Password recovery can be accomplished remotely or physically with software. On windows PC's you can run programs remotely like PWDump and if you have access you can run various kinds of bootable disk to change and recover passwords. Other password recovery methods include running Hash or Sam files recover tools on the PC on the users portfolio. With the SAM file of Hashes you can then proceed to compromise the hash to gain the security.